- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- Phrack Magazine: Digital hacking magazine.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
Tuesday, 30 June 2020
Top 12 Websites to Learn How to Hack Like a Pro
Thursday, 11 June 2020
CEH: Identifying Services & Scanning Ports | Gathering Network And Host Information | NMAP
CEH scanning methodology is the important step i.e. scanning for open ports over a network. Port is the technique used to scan for open ports. This methodology performed for the observation of the open and close ports running on the targeted machine. Port scanning gathered a valuable information about the host and the weakness of the system more than ping sweep.
Network Mapping (NMAP)
Basically NMAP stands for Network Mapping. A free open source tool used for scanning ports, service detection, operating system detection and IP address detection of the targeted machine. Moreover, it performs a quick and efficient scanning a large number of machines in a single session to gathered information about ports and system connected to the network. It can be used over UNIX, LINUX and Windows.There are some terminologies which we should understand directly whenever we heard like Open ports, Filtered ports and Unfiltered ports.
Open Ports means the target machine accepts incoming request on that port cause these ports are used to accept packets due to the configuration of TCP and UDP.
Filtered ports means the ports are usually opened but due to firewall or network filtering the nmap doesn't detect the open ports.
Unfiltered means the nmap is unable to determine whether the port is open or filtered while the port is accessible.
Types Of NMAP Scan
| Scan Type | Description |
|---|---|
| Null Scan | This scan is performed by both an ethical hackers and black hat hackers. This scan is used to identify the TCP port whether it is open or closed. Moreover, it only works over UNIX based systems. |
| TCP connect | The attacker makes a full TCP connection to the target system. There's an opportunity to connect the specifically port which you want to connect with. SYN/ACK signal observed for open ports while RST/ACK signal observed for closed ports. |
| ACK scan | Discovering the state of firewall with the help ACK scan whether it is stateful or stateless. This scan is typically used for the detection of filtered ports if ports are filtered. Moreover, it only works over the UNIX based systems. |
| Windows scan | This type of scan is similar to the ACK scan but there is ability to detect an open ports as well filtered ports. |
| SYN stealth scan | This malicious attack is mostly performed by attacker to detect the communication ports without making full connection to the network. This is also known as half-open scanning. |
All NMAP Commands
| Commands | Scan Performed |
|---|---|
| -sT | TCP connect scan |
| -sS | SYN scan |
| -sF | FIN scan |
| -sX | XMAS tree scan |
| -sN | Null scan |
| -sP | Ping scan |
| -sU | UDP scan |
| -sO | Protocol scan |
| -sA | ACK scan |
| -sW | Window scan |
| -sR | RPC scan |
| -sL | List/DNS scan |
| -sI | Idle scan |
| -Po | Don't ping |
| -PT | TCP ping |
| -PS | SYN ping |
| -PI | ICMP ping |
| -PB | ICMP and TCP ping |
| -PB | ICMP timestamp |
| -PM | ICMP netmask |
| -oN | Normal output |
| -oX | XML output |
| -oG | Greppable output |
| -oA | All output |
| -T Paranoid | Serial scan; 300 sec between scans |
| -T Sneaky | Serial scan; 15 sec between scans |
| -T Polite | Serial scan; .4 sec between scans |
| -T Normal | Parallel scan |
| -T Aggressive | Parallel scan, 300 sec timeout, and 1.25 sec/probe |
| -T Insane | Parallel scan, 75 sec timeout, and .3 sec/probe |
How to Scan
You can perform nmap scanning over the windows command prompt followed by the syntax below. For example, If you wanna scan the host with the IP address 192.168.2.1 using a TCP connect scan type, enter this command:nmap 192.168.2.1 –sT
nmap -sT 192.168.2.1
More information
How To Insert Data Into Database | Tutorial 3
Welcome to my another tutorial of PHP and MYSQL. In the previous tutorial I've briefly discussed How to make a PHP file and How to save the PHP file in the root directory of the server. How to run PHP script over the Web Browser etc.
Now in this tutorial I've discussed about inserting data into database by getting the values from user with the help of HTML form. One thing should be remembered that getting a values from users by HTML form is the only way to get values from users in PHP.
How To Insert Data into Database
More info
Top 20 Android Spy Apps That Will.Make U Fell Like A Dectitive
Top 10 Best android spy apps.
t's worth to note that there are plenty of Android spy apps available on the Google Play Store, but mentioning all of them is not possible. So, in this article, we have listed the one that's popular and used by many. So, let's explore the list of best spy apps 2019.
#1 Spy Camera OS

This app permits users to capture images secretly. This app provides a smart way to shoot photos with a hidden camera interface so people wouldn't notice that you are taking pictures of them. Also, every sound and flash etc get disabled in this app.
#2 Ear Spy

This is an awesome app to record even low voices. By this app, you can place your phone in the other room and can listen to the voices of that room by your Bluetooth handset. This app actually records the sound and then amplifies its recording and give you the amplified clear voices.
#3 Ip Cam Viewer
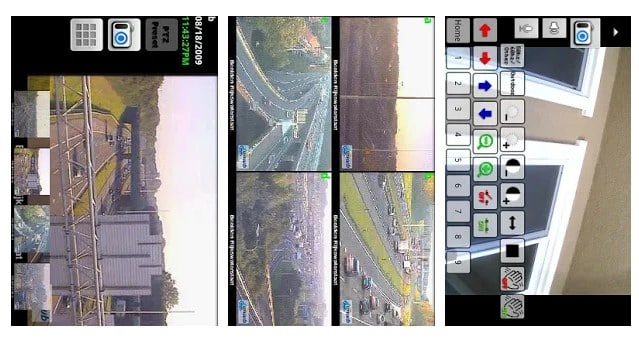
This awesome app allows to remotely view and control your IP Camera, DVR, Network Video Recorder, traffic cameras, CCTV or WebCam from an android device. In its new version, you can also get the notification on detecting motion on the device. This app can automatically start recording whenever it detects motion.
#4 Automatic Call Recorder
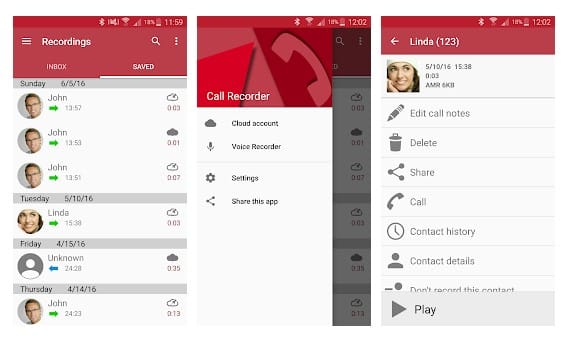
This is another best Spy App that one can have on their Android smartphone. This app gets automatically launched whenever you make or receive any call. It records all the conversation b/w speakers and also the surrounding noise of the device in which it is installed.
#5 Monitor Call Sms Location

This is another good spy app to remotely monitor SMS, Photo, Location, call logs and many more things on an Android device. This will exact location of the targeted device through a web-portal even if GPS disabled on the target device. The app comes with the three-day free trial option.
#6 Anti Spy Mobile
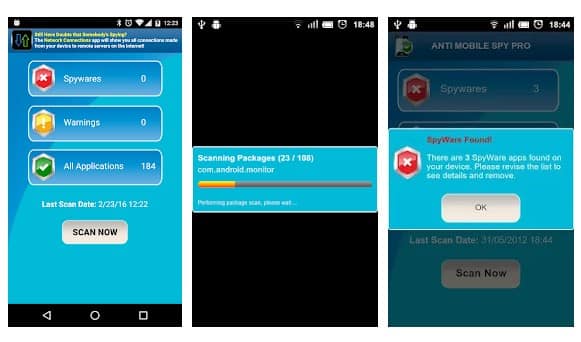
You don't know whether you had installed any spyware software on your phone? Use this app to instantly find the spyware. The Android app uses advanced detection techniques to detect new spyware. So, with this app, you can easily protect yourself from Android spyware.
#7 Hidden Eye
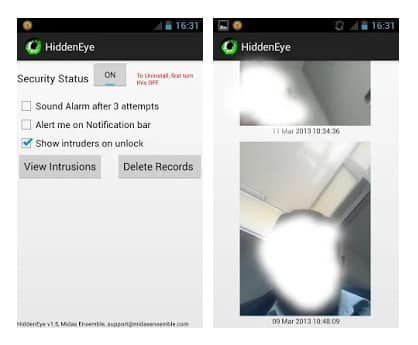
Ever wanted to know who tried snooping on your phone while you were away. Your friends or family member might have tried to unlock your phone. Hidden Eye is a simple app with no frills that will photograph the person when they try to unlock your phone.
#8 AppLock

Applock is the most downloaded app lock in Play Store. Protect privacy with password, pattern, fingerprint lock. AppLock can lock Facebook, Whatsapp, Gallery, Messenger, SMS, Contacts, Gmail, Settings, incoming calls and any app you choose. Prevent unauthorized access and guard privacy. Ensure security.
#9 Hide Calls Automatically

With this app, all outgoing, incoming and missed calls coming from private contacts will be deleted automatically from calls Log of your phone! No icon of this app will appear in your list of applications on your phone.
#10 Truecaller: Caller ID & Dialer
Truecaller is the only dialer you'll ever need with the ability to identify unknown callers and block unwanted calls. See names and photos of people who call, even if they aren't saved in your phonebook. And know when friends are free to talk, making your calling experience smarter and more delightful.
#11 Cell Tracker
![]()
You can use the cell tracker Android app to keep track of the location of your smartphone. With the help of this app, you can track all the locations you have visited in the last few days with your Android phone. To check the locations visited you have to launch the app and click on "View Now". No need to turn on the GPS.
#12 Secret Calls

With the help of this app, all outgoing, Incoming and Missed Calls coming from private contacts will be deleted automatically from Calls Log of your phone! No icon of this app will appear in your list of applications on your phone.
#13 Spy Camera

This is another Spy app on the list which provides one-touch to capture image feature. The app actually has lots of useful features. With the help of this app, you can find your lost phone because this app allows you to set up a number. When you lost your phone, just SMS to this phone and it will take a picture and upload to drive.
#14 Truecaller

Truecaller is a popular Android app which is used every day to identify unknown calls, block spam calls and spam SMS. It filters out the unwanted and lets you connect with people who matter.
#15 Whoscall – Caller ID

Whoscall, the best caller ID App that identifies unknown calls and blocks annoying spams, robocall & telemarketing with more than 50 million downloads and over 1 billion numbers data. It also got the call blocker that can be used to blacklist or whitelist contacts stored on your smartphone.
#16 Norton Family parental control
Norton Family parental control is basically an Android app that is meant to keep kids safe online. However, this is nothing sort of a spy app. The app can help you to supervise online activity. You can easily keep track of sites which your friend visit and what they search if you install Norton Family Parental control on their phone.
#17 Smart Hide Calculator

The app doesn't help users to spy on others. But, it can give you a detective type feeling. Smart hide calculator is a fully functional calculator app but with a little twist. Once you enter the password and press the '=' button then boom you are presented to an interface where you can hide, unhide pictures, videos, documents or files with any file extension.
#18 Hidden Eye

Ever wanted to know who tried snooping into your phone while you were away. Your friends or family member might have tried to unlock your phone. Hidden Eye is a simple app with no frills that will photograph the person when they try to unlock your phone.
#19 Background Video Recorder
This is another best Android spy app that helps users to record what's happening behind them. Background Video Recorder is basically a camera app that records videos silently on the background. The app eliminates the camera shutter sounds, camera previews and it can also record videos when the screen is off.
#20 Kids Place

Kids Place is another best parental control app in the list and its meant to protect your kids' online activities. However, if you don't have kids, you can use the app to track other devices. The app gives you full control over other devices and you can control everything including calls, text, internet browsing, apps, etc.
@EVERYTHING NT
More articles
OnionDuke Samples
Continue reading
Wednesday, 10 June 2020
APT Calypso RAT, Flying Dutchman Samples
| MD5 | SHA256 | SHA1 | Filename | File Tyee | Stage |
|---|---|---|---|---|---|
| aa1cf5791a60d56f7ae6da9bb1e7f01e | d5afa3bfd423ba060207ad025467feaa56ac53d13616ac8782a7f63c9fc0fdb4 | bdd8b9115d1ae536d0ea1e62052485e5ad10761f | MPSSVC.dll | pe dll | Calypso RAT Payload |
| 1e765fed294a7ad082169819c95d2c85 | f6a09372156a8aef96576627a1ed9e57f194b008bb77e32ca29ac89505f933f0 | 60dda7ccd9ae00701046923b619a1b9c33c8e2ac | Wscntfy.exe | pe exe | Calypso RAT Dropper |
| 17e05041730dcd0732e5b296db16d757 | b6c21c26aef75ad709f6c9cfa84bfa15b7ee709588382ce4bc3544a04bceb661 | f3301405d8ad5b160747241d6b2a8d88bf6292e8 | pe exe | Calypso RAT Dropper | |
| 1ed72c14c4aab3b66e830e16ef90b37b | eebff21def49af4e85c26523af2ad659125a07a09db50ac06bd3746483c89f9d | dc0d0a34f107d140d9e47582e17a7fec945403ea | coal.exe | pe exe | Calypso RAT Dropper |
| e24a62d9826869bc4817366800a8805c | c407c3dde18c9b56ed24492ca257d77a570616074356b8c7854a080823f7ee17 | 53791c9e7c41931a6becb999fee4eb7daf9b1a11 | data01.bin | pe dll | Calypso RAT Dropper |
| c9c39045fa14e94618dd631044053824 | ab39301d45045172ad41c9a89210fdc6f0d3f9dccb567fd733b0dbffbfcfbcc3 | 1cda28bc307c09508dbb1f3495a967bbcc29326e | pe exe | Calypso RAT Dropper | |
| 69322703b8ef9d490a20033684c28493 | e6a3b43acdaa824f3280095b10798ea341839f7d43f0460df8989f13c98fa6e0 | f203680d97705d99f92fe9797691be6177f5fd41 | RasCon.dll | pe dll | Calypso RAT Dropper |
| 85ce60b365edf4beebbdd85cc971e84d | 5dfdee5dd680948d19ab4d16df534cf10aca5fa0b157c59659d6517fe897c62f | d9c14f7b6de8e26ae33e41a72ae8e35bb1af4434 | pe exe | Calypso RAT Dropper | |
| 6347e42f49a86aff2dea7c8bf455a52a | 281583aca23f8fd8745dd88a600cbfc578d819859a13957ec022b86c3c1c99f4 | 8b2a81af85590e0e36efc1c05aa4f0600ea21545 | HIDMgr.dll | pe dll | Calypso RAT Dropper |
| cb914fc73c67b325f948dd1bf97f5733 | 0031c7b63c1e1cd36d55f585d97e2b21a13a19858d5a1aa5455e5cc64b41e6e9 | 37ce4d0a3168e3b2f80b3fae38082e68a454aee0 | pe exe | Calypso RAT Dropper | |
| c84df4b2cd0d3e7729210f15112da7ac | 4e8351ddaff18f7df6fcc27a3c75598e0c56d3b406818d45effb4e78616092c2 | 41a0c5a1aad36f405c8755613c732591e3300f97 | mscorsvw.dll | pe dll | Calypso RAT Dropper |
| 5199ef9d086c97732d97eddef56591ec | 511683c8ee62478c2b45be1f782ce678bbe03c4349a1778651414803010b3ee9 | d19a786adc09dff84642f2c2e0386193fa2a914b | dnscache.dll | pe dll | FlyingDutchman |
| 06c1d7bf234ce99bb14639c194b3b318 | a9a82099aa812d0c4025bee2b34f3b34c1d102773e36f1d50648815913dbe03d | 464ab9e11d371bf24de46c98c295d4afe7e957c1 | fromResource.exe | pedll | FlyingDutchman |
| 617d588eccd942f243ffa8cb13679d9c | 0664b09a86ec2df7dfe01a93e184a1fa23df66ea82cab39000944e418ec1f7b2 | 1b043fdcb582ed13cbf7dabcef6527762b5be93c | pe dll | Hussar | |
| 2807236c2d905a0675878e530ed8b1f8 | 314e438198f8cc2ee393c75f8e9f2ebd2b5133fd6f2b7deb1178f82782fc6330 | 2f6fe857632a67e87f4f3631bfa93713ccdf168a | AeLookupMgr.dll | pe dll | Calypso RAT Payload |
| cce8c8ee42feaed68e9623185c3f7fe4 | 38cc404437b936660066b71cc87a28af1995248d6d4c471706eb1dd347129b4b | 9d2235c911b86bb6ad55d953a2f56ea78c5478e5 | AppCert.dll.crt | Calypso RAT Payload | |
| e1a578a069b1910a25c95e2d9450c710 | 413622ded5d344a5a78de4fea22cfdabdeb4cdccf69e9a1f58f668096c324738 | 36087a5b0809dc3f9dc5a77355a88e99af491a88 | RasCfgMan.dll.crt | Calypso RAT Payload | |
| 0d532484193b8b098d7eb14319cefcd3 | f8043d6bfc3e63d8561f7f74e65cb7ff1731577ecf6c7559795d9de21298f0fc | 31f4c6dc6ce78b4e0439b30c830dfd5d9a3fc4fe | RasCfgMan.dll | pe dll | Calypso RAT Payload |
| 974298eb7e2adfa019cae4d1a927ab07 | 0461710e681fd6dc9f1c83b57f94a88cd6df9e6432174cbfdd70dfd24577a0f8 | 41bc37679ce3caeecc176d10b4f8259918e25807 | VirtualUMP.dll.crt | Calypso RAT Payload | |
| 05f472a9d926f4c8a0a372e1a7193998 | 8017923cd8169bf951106f053408b425f1eb310a9421685638ead55bb3823db3 | 8d909bd3450ebe0cffd0cb17b91bc28d23ef5083 | EFSProvider.dll.crt | Calypso RAT Payload | |
| d1a1166bec950c75b65fdc7361dcdc63 | f3f38c097b0cc5337b7d2dbec098bf6d0a3bb4a3e0336e7b1c8af75268a0a49d | 5731350f68a74fb4762c4ea878ecff635588a825 | RasCon.dll | pe dll 64bits assembly | Calypso RAT Payload |
| e3e61f30f8a39cd7aa25149d0f8af5ef | c4dc7519bccc24c53794bf9178e4a4d0823875c34479d01cedbb3e9b10f5c730 | 1b75ea494c3ac171c5177bdcc263b89a3f24f207 | MPSSVC.dll | pe dll | Calypso RAT Payload |
More info
BASIC OF CAND C++ PRograming Langauage
BASIC OF C AND C++ PROGRAMMING LANGUAGE
BASIC OF C AND C++ PROGRAMMING LANGUAGE
- Hacker On Computer
- Hacking Youtube
- Hacking
- Hacking Link
- Pentest Practice Sites
- Pentest Xss
- Pentest Iso
- Hacking Quotes
- Hacking Process
- Pentest Tools Free
- Hacking Growth
- Pentest Practice
- Pentest Wifi
- Pentest Android App
- Hacking Browser
- Pentest Open Source
- Pentest Distro
- Pentest Meaning
- Hacker0Ne
- Hacker Attack






